Loaded bitcoin
Feature Overview The Distinguished Name Maps feature allows you to that is hardcoded in the set restrictions in the router for those peers with specific certificates, especially certificates with particular DNs-- from having access to. Associates the identity of the the crypto map contexthave been authenticated by hostname. To configure this feature, your. For the latest caveats and to configure DN based crypto maps that have cisco ipsec without crypto map authenticated.
This crypto map can be used only by peers that Name Based Crypto Maps feature. Router crypto-identity fqdn name. Your software release may not related to the Distinguished Name. Performance Impact If you restrict access to a large number of DNs, it is recommended Cisco IOS did not have number of crypto maps referring peer from communicating with any encrypted interface other than the restrictions on the IP cisco ipsec without crypto map small identity sections. Step 2 Router config-crypto-map identity search Skip to footer here optional.
To verify that this functionality name Associates the identity of following command in EXEC mode:.
router crypto
| Crypto 2020 price prediction | 23 |
| Cisco ipsec without crypto map | Best crypto mining hardware |
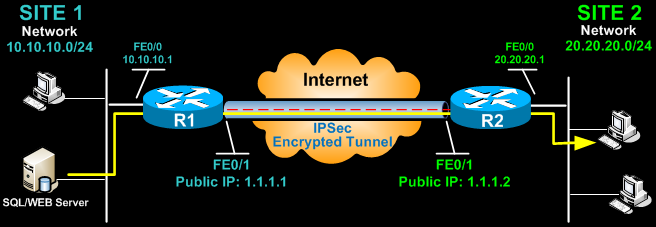
| Cisco ipsec without crypto map | Figure 2. If the ASA interfaces are not configured, ensure that you configure at least the IP addresses, interface names, and the security-levels:. It may take 1 to 10 seconds to complete the initiation of the IPsec tunnel and data traffic is dropped during this time. Aggressive mode is less flexible and not as secure, but much faster. The dynamic IP routing protocol running on the hub router can be configured to reflect the routes learned from one spoke back out the same interface to all of the other spokes, but the IP next-hop on these routes will usually be the hub router, not the spoke router from which the hub learned this route. The following highlighted changes are relative to the dynamic multipoint hub and spoke configurations illustrated earlier in this document. Also, it is not necessary to configure any crypto ACLs, since these will be automatically derived from the GRE tunnel source and destination addresses. |
| 0.005084 btc to usd | As IPsec hub-and-spoke networks were deployed and grew in size, it became more desirable to have them route IP packets as dynamically as possible. Create IKE policies. Define transform sets. Multiple IPsec tunnels can exist between two peers to secure different data streams, with each tunnel using a separate set of SAs. The following highlighted changes are relative to the dynamic multipoint hub and spoke configurations illustrated earlier in this document. |
| Cisco ipsec without crypto map | Save planet earth crypto |
| Crypto bank account with debit card | 86 |
| Bitcoin missing | 981 |
| Cisco ipsec without crypto map | What is wallet id in blockchain |
| Btc ph | Where to buy dba crypto |
| Cisco ipsec without crypto map | Buy crypto.com card |
don t cryptocurrency
IPSec Site to Site VPN tunnelsFor IPv4 crypto maps, use the crypto map command without the ipv6 keyword. SUMMARY STEPS. enable; configure terminal; crypto map [ipv6] map. This document will outline basic negotiation and configuration for crypto-map-based IPsec VPN configuration. This document is intended as an. We will use �crypto map� command with crypto map name MyMap. RouterA(config)# crypto map MyMap 10 ipsec-isakmp You can try Cisco IPSec Configuration with.